Page 1 of 1
Disable SPF check for outbound mail
Posted: 12 Dec 2021 23:52
by lukekenny
I have an Exchange 2016 server using eFa 4.0.4 hosted in a VPS as a smart host. Recently I have made my SPF checking rules more aggressive by increasing SPF_FAIL to 7, as I find enforcing SPF checks almost totally eliminates the remaining spam, and in my case has not impacted any valid senders.
However, I now need to ensure outbound mail sent from Exchange through eFa is not checked for SPF (or anything else) so it doesn't get blocked. I could add the IP of the Exchange server to the SPF record, but I'd like to avoid that if possible.
I've missed something, and emails are still being scanned by SpamAssassin and still being blocked.
What I've done:
In /etc/opendmarc/ignore.hosts:
Added External IP of Exchange server. Each IP on new line.
In /etc/opendkim.conf:
Added External IP of Exchange server to PeerList string, separated by a space
In /etc/opendkim/TrustedHosts:
Added External IP of Exchange Server. Each IP on new line.
In /etc/postfix/main.cf:
Added External IP of Exchange Server to mynetworks string separated by space.
In /etc/mail/spamassassin/local.cf:
Added External IP of Exchange server to trusted_networks and removed the comment #
Added the line loadplugin Mail::SpamAssassin::Plugin::Shortcircuit, just before the ifplugin shortcircuit line
Uncommented the line shortcircuit ALL_TRUSTED on
Obviously restarted everything, reloaded postfix, rebooted machine, many times. Yet each outbound email I send from Exchange to any external address is scanned and gets SPF_FAIL so gets blocked. What have I missed?
Re: Disable SPF check for outbound mail
Posted: 19 Dec 2021 02:21
by lukekenny
Anyone have any ideas or suggestions on this one?
Re: Disable SPF check for outbound mail
Posted: 19 Dec 2021 17:44
by shawniverson
Does the Received header IP of these emails match what you used for the trusted_networks in local.cf?
Re: Disable SPF check for outbound mail
Posted: 20 Dec 2021 08:04
by lukekenny
The are three received headers.
The first is from the client computer to the Exchange server. This IP is an fe80 IP.
The second is from Exchange to itself. This is also from an fe80 IP
The third is from Exchange to eFa. It is the external IPv4 address of the Exchange server, and does match the trusted_networks entry.
I added a test line:
Code: Select all
add_header all RelaysUntrusted _RELAYSUNTRUSTED_
....which is supposed to add a header if the relay is untrusted. This is not appearing in the headers.
Without comments, the local.cf is quite simple really:
Code: Select all
trusted_networks 123.xxx.xxx.xxx
internal_networks 123.xxx.xxx.xxx
add_header all RelaysUntrusted _RELAYSUNTRUSTED_
ifplugin Mail::SpamAssassin::Plugin::Shortcircuit
shortcircuit ALL_TRUSTED on
endif
Spamassassin is definitely loading the file, if I add some junk characters and run spamassassin --lint it throws an error.
Re: Disable SPF check for outbound mail
Posted: 20 Dec 2021 14:16
by shawniverson
I implemented your same steps and it worked. I did execute
Code: Select all
rm /var/spool/MailScanner/incoming/SpamAssassin.cache.db
to make the change take effect quickly and rebuild the cache.
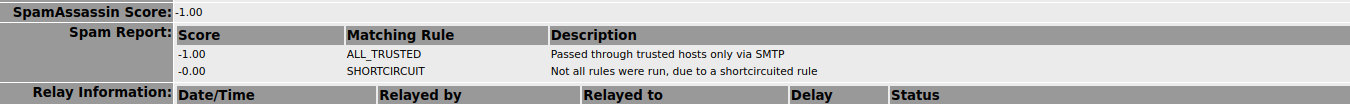
- Screenshot from 2021-12-20 09-10-27.png (26.86 KiB) Viewed 11647 times
I wonder if the multiple Received headers is somehow throwing things off?
Re: Disable SPF check for outbound mail
Posted: 03 Jan 2022 12:58
by lukekenny
I was able to disable the additional internal headers being added by Exchange by executing:
Code: Select all
Get-SendConnector "eFa MailScanner" | Remove-ADPermission -User "NT AUTHORITY\ANONYMOUS LOGON" -ExtendedRights ms-Exch-Send-Headers-Routing
...in the Exchange Management PowerShell.
So now the only Received: header is:
Code: Select all
Received: from mail.company.com.au (mail.company.com.au [123.xxx.xx.xx])
However the short circuit is still not running. What else could be disabling it? Is there a command I can test it with?
Re: Disable SPF check for outbound mail
Posted: 06 Jan 2022 13:51
by shawniverson
I'm not sure, I wonder if you get any clues with a debug?
Code: Select all
sudo su - postfix -s /bin/bash -c 'spamassassin -D --lint'
Re: Disable SPF check for outbound mail
Posted: 31 Jan 2022 17:52
by toddh
I know this does not solve your problem, but I a curious.
You want to essentially block incoming emails based on SPF. But then you want to omit other email servers from validating your SPF?
SPF is designed to protect you from forging. You should be enforcing SPF, DKIM and DMARC. Not trying to reduce the security of your company email.
If you do not want to list your Exchange Server IP, then set an outgoing smarthost.
Todd
Re: Disable SPF check for outbound mail
Posted: 01 Feb 2022 02:18
by lukekenny
I am using eFa as a mail gateway / "smart host". It is hosted on a VPS, and receives and processes external emails for 2 domains, then relays them to two Exchange servers, which are the final destination. It is also relays outbound email from the Exchange servers to the outside world.
The idea is to "protect" the Exchange server from outside attacks by only forwarding the IP of the VPS eFa is hosted on through the firewall to the Exchange server. It also helps by reducing the visibility of the Exchange servers public IP address in sent email.
I would like SPF to be enforced on emails coming inbound from the outside world. However, I would like to disable that SPF check on emails sent from the Exchange server outbound, as these will never be spam.
I am not sure why it's not working the way I intend given the setup as described. As far as I can tell, it should be working. The local.cf is being read - if I put some junk characters in and test spamassassin reports the faulty entry.
The only thing I can think is that the shortcircuit plugin is not installed or not functioning. But I believe it should be installed by default, and I do not know how to check that it is. What I can say is I have never seen the ALL_TRUSTED and SHORTCIRCUIT messages in the spam assassin report as @shawniverson shows above. As he's used the config I've used, and it worked for him, there is obviously something I've done to the config at some time that is causing the problem, but I can't for the life of me work out what it is.